License Auditing Usage Management Tool
Loading DocCommentXchange. Loading DocCommentXchange. The Haunted Versus Rapidshare there. Learn how to fasttrack your company to software license compliance through an effective software asset management discipline. Optimize software licensing. In the field of computer network administration, pcap packet capture consists of an application programming interface API for capturing network traffic. Guidelines for quality andor environmental management systems auditing. CPU usage. 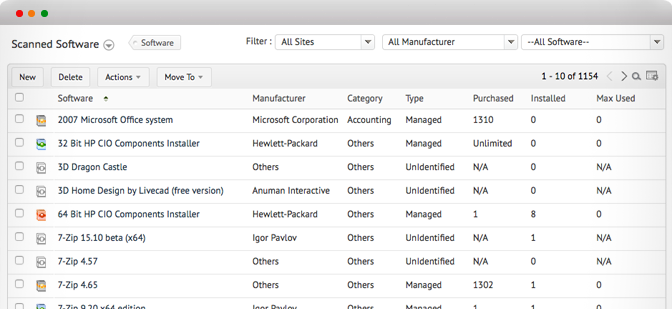
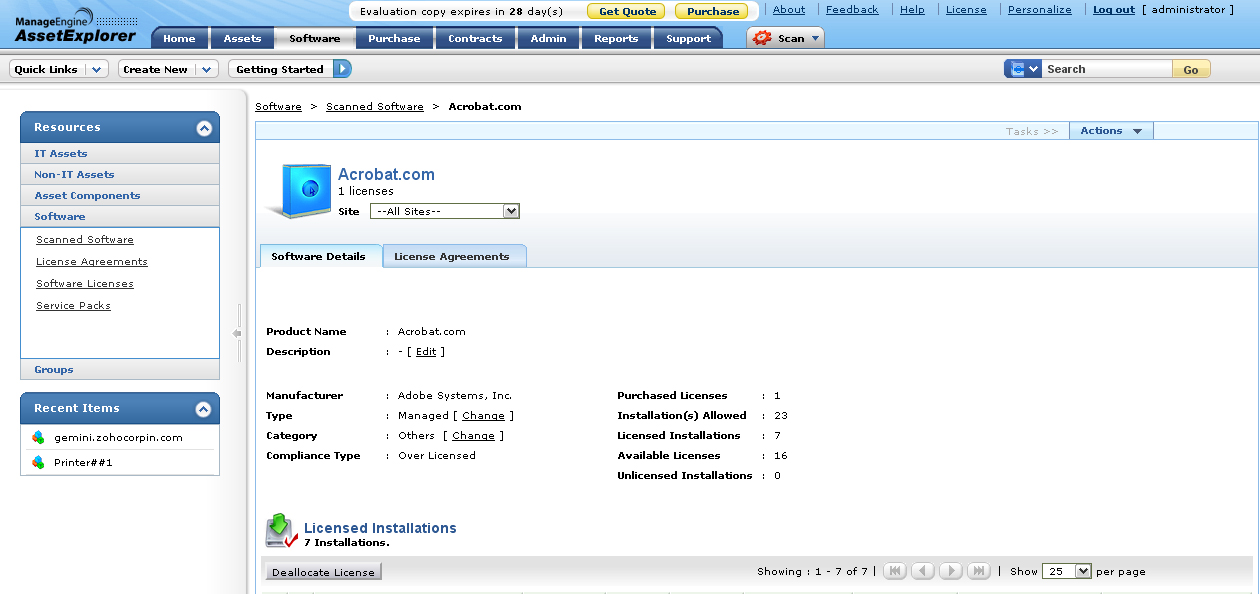 Software License Compliance Five Essential Steps. According to the 2. Global Software Piracy Study published by the Business Software Alliance BSA, nearly one out of five software programs put into service in the United States is illegal. The subject of software piracy, and how software is pirated, was commonly misunderstood by many not so long ago. But vigorous efforts over the last two decades by two software industry trade associations, the Business Software Alliance and the Software Information Industry Association SIIA, and by individual software vendors has improved the level of awareness if not understanding on the issue. Common Forms of Corporate Piracy. GUI administration tool for Ldap management, control and development. Both windows and Linux versions are available. In the workplace, employees sometimes share copies of company software with each other without going through proper channels to obtain licensed copies. Or they may bring personal copies from home to work and load them onto their computers. These actions are common forms of software piracy that are often carried out with little or no forethought about anything other than the need to accomplish work on schedule. Employees look for the most convenient way of getting things done. They also sometimes download unlicensed software from the Internet. Although the employees may not have intended to commit piracy, their actions can still put an organization at risk. Other acts of software piracy can occur when an organization expands or changes personnel. Licensing details can be forgotten or overlooked during times of change, leading to careless installs of unlicensed software. Especially in times of economic downturn, organizations might engage in cost cutting practices that lead to unlicensed use of software. Pirated software is not simply software that has been counterfeited for resale, but includes any unlicensed use of software by individuals in any setting. But, thankfully, there are steps that you can take to protect yourself from legal exposure and risk. This Licensing Information document is a part of the product or program documentation under the terms of your Oracle license agreement and is intended to help you. Find and compare IT Asset Management software. Free, interactive tool to quickly narrow your choices and contact multiple vendors. Great 3rd party addon tools to augment MYOB Business Management Software. Windows Active Directory Reports. Reports on Windows Active Directory arm an administrator with essential information on Active Directory Infrastructure and Objects. Top Leading Oracle Training in Chennai by Certified Experts. Recommended as Best Oracle Training Institute in Chennai with placements. Excellent Oracle training. The Fast Track to Software License Compliance. Collect proofs of ownership. License Auditing Usage Management Tool' title='License Auditing Usage Management Tool' />Purchase orders. Paid invoices. Retail and other receipts for purchase. Volume purchase licensing contracts. Original license certificates. When identifying proofs of ownership care should be taken to avoid overlap in the various proofs used to demonstrate software license compliance. Purchase orders, paid invoices and receipts for purchase should be checked to determine whether they refer to a common purchase or to separately licensed copies. Likewise, with Volume Purchasing Contracts if you use mixed proofs to justify separately licensed software you must be able to demonstrate that they do not refer to the same transaction. Atomic Mail Sender 8 Cracked. Original License Certificates are unique and generally associated with retail purchased software. These certificates presumably demonstrate that you have obtained a legitimate copy of the software but this assumes that the certificate is not counterfeit, and that it has come into your possession through a purchase. Certificates are actually not a very strong proof of ownership, even if rarely disputed in practice. Microsoft informs us in their SAM Brief that Proof of License for Microsoft Software typically consists of a paid invoice or receipt in either an electronic or physical form it provides proof that your organization bought the licensed software from Microsoft or an authorized reseller and that the software license was paid for. Proof of ownership comes down to purchase records show me the money. Serial numbers are not proofs of ownership. They are useful to identify copies of software and their source and they are sometimes helpful when purchasing upgrades. But auditors will not accept the existence of serial numbers as proof of ownership. Additionally, original media CDs, diskettes, and documentation is less useful in todays world of volume purchase contracts and multiple license packs, and is generally unreliable in counting numbers of licenses. Audit Installed Software. Systematically inspect every Desktop. Portable. Virtual computer. Server. Personal computerdevice used for company purposes. Steps one and two can be reversed or carried out simultaneously proofs of ownership and software audits. Both must be completed prior to reconciling and proving license ownership in step three. You will need an exhaustive list of all copies of software and their version numbers installed on all computers in your organization. Later we will discuss tools that you can use for this task. Once you have completed steps one and two you are ready to discover how much of your organizations installed software is legally licensed. Personally owned computers used for work pose a special problem. Such devices may have a mix of software purchased personally and by the company. Whether an outside audit would or would not have access or jurisdiction over these devices is not always clear. But such jurisdiction can be associated with software licensing agreements that grant secondary use rights the right of a user to install and use the software from a second device. But here we are focusing on an internal company compliance effort, so company policies regarding personal devices used at work should be clearly stated and enforced. Reconcile the Software Audit Proof of Ownership records. Compare and match the following items Software Product Names. Version Numbers. Types of Licenses Per device, Per user, Concurrent use, other modelsCompare the items in list three between your audit list and ownership proofs list for matches. The goal of step three is to discover any software installed or in use within your organization that cannot be traced back to an acquired license. And when it can be traced to a license, you must note whether your organization has acquired sufficient entitlements to cover all copies discovered in the audit. When unlicensed software is discovered, you must decide whether to buy a license or delete the software. Thats it in a nutshell youve established momentary compliance. This is easy to describe, extremely difficult to accomplish unless you employ the use of automated auditing and usage management tools more on that subject later. A Long term Solution Steps 4 5. Establish Corporate Culture. Publish corporate policy. Have employees agree to and sign it. Centralize purchases. Store purchase contracts, license certificates, purchase orders, invoices, receipts. The Fall Of Hyperion Pdf on this page. Detect and manage employee software installs. There is nothing that can replace the value of well designed and active anti piracy education among all members of your organization. Their understanding of the liability and the policies that address it will go a long way toward reducing risk. Add to that the organizational discipline of recording ownership as purchases occur and you will create the important foundational basis upon which your company can build an effective software license compliance program. Manage Ongoing Usage. Determine ownership department, division, or corporateManage correctly by type of entitlement. Who should have access to each software product Identify waste, reclaim redistribute. Predict needs and purchase accordingly. Track computer obsolescence and stop buying software. Track software usage and analyze for optimization and cost reduction. Before you can effectively manage software usage to comply with your software licenses you must first know who owns the licenses.
Software License Compliance Five Essential Steps. According to the 2. Global Software Piracy Study published by the Business Software Alliance BSA, nearly one out of five software programs put into service in the United States is illegal. The subject of software piracy, and how software is pirated, was commonly misunderstood by many not so long ago. But vigorous efforts over the last two decades by two software industry trade associations, the Business Software Alliance and the Software Information Industry Association SIIA, and by individual software vendors has improved the level of awareness if not understanding on the issue. Common Forms of Corporate Piracy. GUI administration tool for Ldap management, control and development. Both windows and Linux versions are available. In the workplace, employees sometimes share copies of company software with each other without going through proper channels to obtain licensed copies. Or they may bring personal copies from home to work and load them onto their computers. These actions are common forms of software piracy that are often carried out with little or no forethought about anything other than the need to accomplish work on schedule. Employees look for the most convenient way of getting things done. They also sometimes download unlicensed software from the Internet. Although the employees may not have intended to commit piracy, their actions can still put an organization at risk. Other acts of software piracy can occur when an organization expands or changes personnel. Licensing details can be forgotten or overlooked during times of change, leading to careless installs of unlicensed software. Especially in times of economic downturn, organizations might engage in cost cutting practices that lead to unlicensed use of software. Pirated software is not simply software that has been counterfeited for resale, but includes any unlicensed use of software by individuals in any setting. But, thankfully, there are steps that you can take to protect yourself from legal exposure and risk. This Licensing Information document is a part of the product or program documentation under the terms of your Oracle license agreement and is intended to help you. Find and compare IT Asset Management software. Free, interactive tool to quickly narrow your choices and contact multiple vendors. Great 3rd party addon tools to augment MYOB Business Management Software. Windows Active Directory Reports. Reports on Windows Active Directory arm an administrator with essential information on Active Directory Infrastructure and Objects. Top Leading Oracle Training in Chennai by Certified Experts. Recommended as Best Oracle Training Institute in Chennai with placements. Excellent Oracle training. The Fast Track to Software License Compliance. Collect proofs of ownership. License Auditing Usage Management Tool' title='License Auditing Usage Management Tool' />Purchase orders. Paid invoices. Retail and other receipts for purchase. Volume purchase licensing contracts. Original license certificates. When identifying proofs of ownership care should be taken to avoid overlap in the various proofs used to demonstrate software license compliance. Purchase orders, paid invoices and receipts for purchase should be checked to determine whether they refer to a common purchase or to separately licensed copies. Likewise, with Volume Purchasing Contracts if you use mixed proofs to justify separately licensed software you must be able to demonstrate that they do not refer to the same transaction. Atomic Mail Sender 8 Cracked. Original License Certificates are unique and generally associated with retail purchased software. These certificates presumably demonstrate that you have obtained a legitimate copy of the software but this assumes that the certificate is not counterfeit, and that it has come into your possession through a purchase. Certificates are actually not a very strong proof of ownership, even if rarely disputed in practice. Microsoft informs us in their SAM Brief that Proof of License for Microsoft Software typically consists of a paid invoice or receipt in either an electronic or physical form it provides proof that your organization bought the licensed software from Microsoft or an authorized reseller and that the software license was paid for. Proof of ownership comes down to purchase records show me the money. Serial numbers are not proofs of ownership. They are useful to identify copies of software and their source and they are sometimes helpful when purchasing upgrades. But auditors will not accept the existence of serial numbers as proof of ownership. Additionally, original media CDs, diskettes, and documentation is less useful in todays world of volume purchase contracts and multiple license packs, and is generally unreliable in counting numbers of licenses. Audit Installed Software. Systematically inspect every Desktop. Portable. Virtual computer. Server. Personal computerdevice used for company purposes. Steps one and two can be reversed or carried out simultaneously proofs of ownership and software audits. Both must be completed prior to reconciling and proving license ownership in step three. You will need an exhaustive list of all copies of software and their version numbers installed on all computers in your organization. Later we will discuss tools that you can use for this task. Once you have completed steps one and two you are ready to discover how much of your organizations installed software is legally licensed. Personally owned computers used for work pose a special problem. Such devices may have a mix of software purchased personally and by the company. Whether an outside audit would or would not have access or jurisdiction over these devices is not always clear. But such jurisdiction can be associated with software licensing agreements that grant secondary use rights the right of a user to install and use the software from a second device. But here we are focusing on an internal company compliance effort, so company policies regarding personal devices used at work should be clearly stated and enforced. Reconcile the Software Audit Proof of Ownership records. Compare and match the following items Software Product Names. Version Numbers. Types of Licenses Per device, Per user, Concurrent use, other modelsCompare the items in list three between your audit list and ownership proofs list for matches. The goal of step three is to discover any software installed or in use within your organization that cannot be traced back to an acquired license. And when it can be traced to a license, you must note whether your organization has acquired sufficient entitlements to cover all copies discovered in the audit. When unlicensed software is discovered, you must decide whether to buy a license or delete the software. Thats it in a nutshell youve established momentary compliance. This is easy to describe, extremely difficult to accomplish unless you employ the use of automated auditing and usage management tools more on that subject later. A Long term Solution Steps 4 5. Establish Corporate Culture. Publish corporate policy. Have employees agree to and sign it. Centralize purchases. Store purchase contracts, license certificates, purchase orders, invoices, receipts. The Fall Of Hyperion Pdf on this page. Detect and manage employee software installs. There is nothing that can replace the value of well designed and active anti piracy education among all members of your organization. Their understanding of the liability and the policies that address it will go a long way toward reducing risk. Add to that the organizational discipline of recording ownership as purchases occur and you will create the important foundational basis upon which your company can build an effective software license compliance program. Manage Ongoing Usage. Determine ownership department, division, or corporateManage correctly by type of entitlement. Who should have access to each software product Identify waste, reclaim redistribute. Predict needs and purchase accordingly. Track computer obsolescence and stop buying software. Track software usage and analyze for optimization and cost reduction. Before you can effectively manage software usage to comply with your software licenses you must first know who owns the licenses.